Visibility and control of the authorized devices on your networks.
One of the pillars of a modern Zero Trust Architecture is understanding the health and status of all authorized devices and using that information to control access and inform risk decisions. VirnetX Matrix provides you with an easy to use device dashboard to gain visibility and control of the authorized devices on your networks.
Real-time Device Insights
From the VirnetX One Admin Console, you can view quick insights into all the authorized devices across your organization. Authorized devices encompass all devices where the VirnetX One Mobile & Desktop client is installed and registered by an authorized user.
From the Devices Summary page, you’ll be able to see the total devices, the change in the number of devices over time and a detailed break-down based on operating system. This information updates in real-time so you can monitor what's happening on your networks.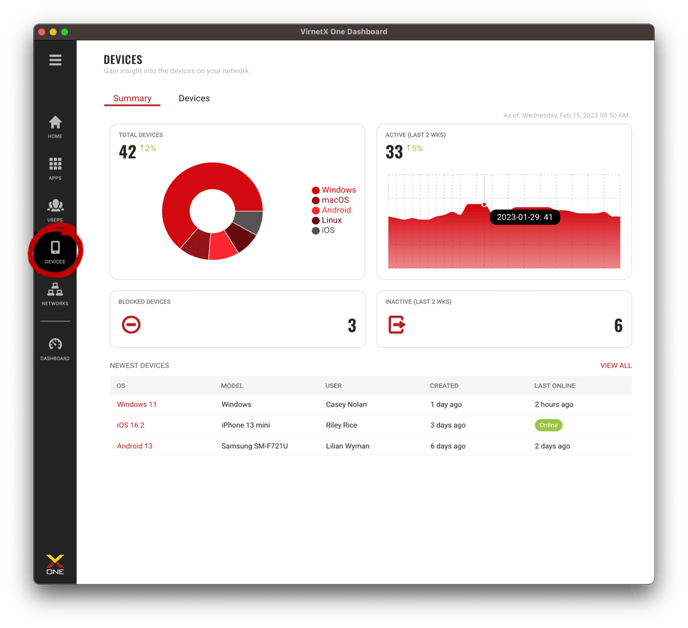
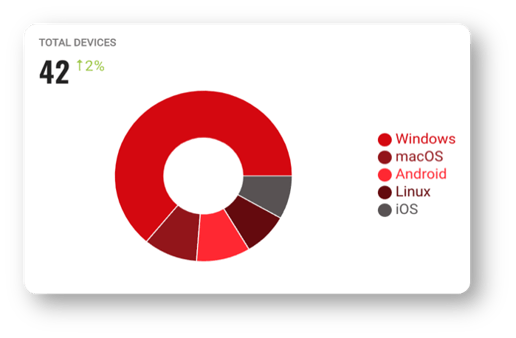
Total Devices By Operating System
You can quickly see the total number of devices, the change in the total over the last day and a breakdown by operating system. Hover over the chart segments to see the exact number of devices for each OS.
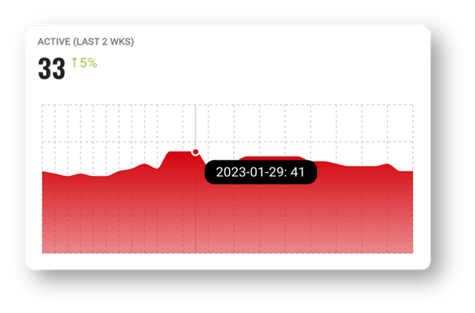
Active Devices on Your Networks
With this chart, you can quickly see the active devices on your network over time and currently on your network. Hover over the chart to see data points from specific dates.
The active device chart shows the rolling total of active devices over the last two weeks from the date of the data point. In the example below, there were 41 total active devices from the two weeks prior to January 29th.
An active device is an authorized device (e.g., laptop, mobile) registered to a user of your organization that has an active VirnetX One platform connection. With an active connection the device can access any user authorized applications, services or infrastructure secured by VirnetX Matrix.
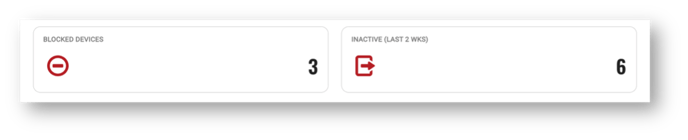
Blocked and Inactive Devices
Quickly gain insights into blocked or inactive devices on your networks.
A blocked device is an authorized device that has been temporarily blocked by an administrator from accessing any application, services or infrastructure secured by VirnetX Matrix.
Inactive devices are authorized devices that have not had an active VirnetX One platform connection in the last two weeks. Based on security policy, after thirty (30) days of inactivity these devices will automatically lose all access to VirnetX Matrix secured applications. Authorized users can reactivate these devices if necessary.
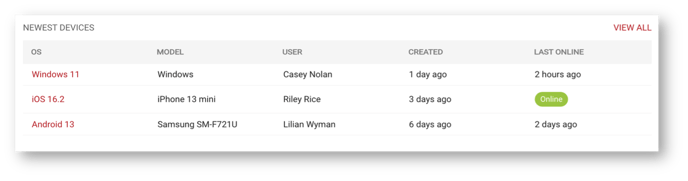
New Devices on Your Network
With this list you can quickly monitor the latest registered devices along with the user that registered the device. Click on an individual device to view all the details or click View All to view the entire device inventory list.
Device Inventory and Reporting
Device inventory is an important component of a Zero Trust Architecture to assess and monitor devices on your network. From the VirnetX One Admin Console, administrators can search, sort, and quickly filter devices based on device attributes, owner, online status, and blocked state. Access the device inventory by clicking Devices icon in the left sidebar menu and then click the Devices tab at the top. The default view shows all the devices in your inventory.
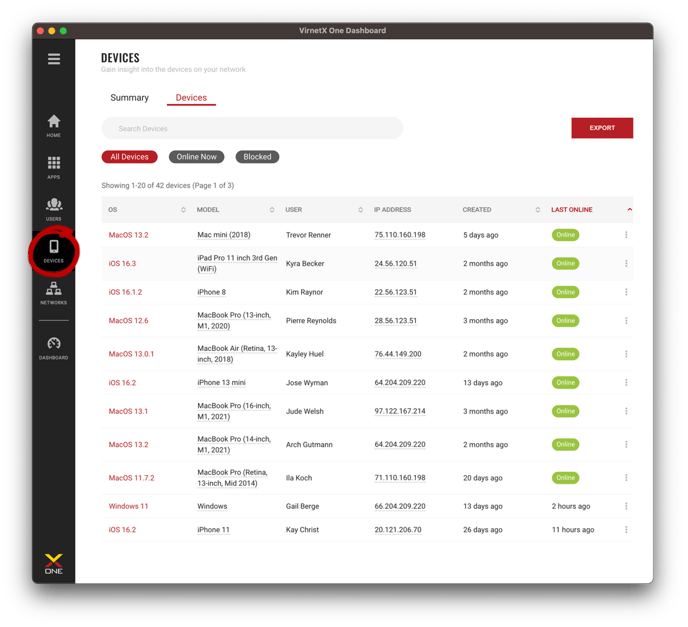
You can sort the results by clicking on any of the data columns (e.g., OS, model, user, etc) to sort either ascending or descending. By default, results are sorted by created date.
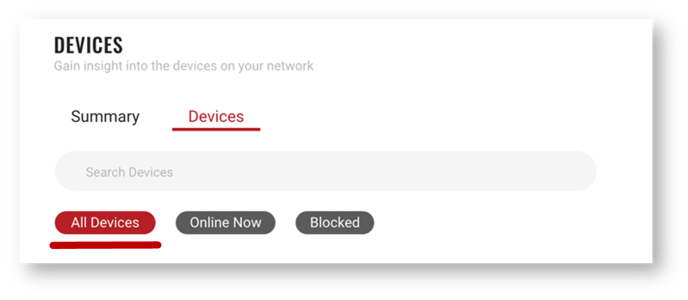
Search and filter devices
From the search box, you can quickly find devices based on operating system (e.g., Windows) or model (e.g., iPhone 11). Below the search box, is a set of filters you can click to refine your search based on all devices, online devices or blocked devices.
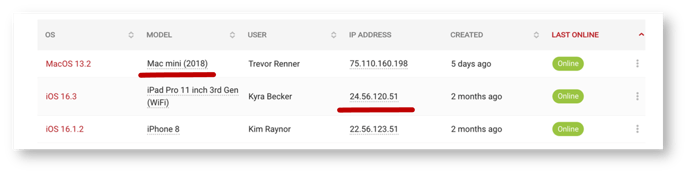
 Quick filtering without typing is also available by clicking on a specific device model or IP address from the list of devices. Properties that can be quick filtered with a click are denoted with a dotted underline.
Quick filtering without typing is also available by clicking on a specific device model or IP address from the list of devices. Properties that can be quick filtered with a click are denoted with a dotted underline.
 Export Device Inventory
Export Device Inventory
Administrators can export their real-time device inventory to a CSV file for reporting, compliance, risk management or security analysis purposes. The exported CSV file includes all device attributes, information about the owner of the device, connection details, network information and security related attributes. The device inventory can be exported all at once or filtered to export a group of devices using the search and filter features.
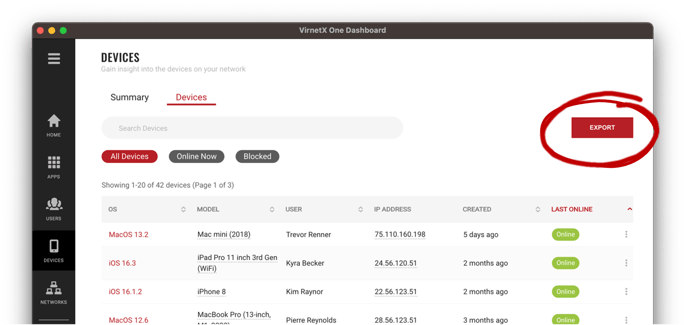
Under the Devices tab, click on the Export button in the top right corner and select Export All Devices to export all devices within your inventory:
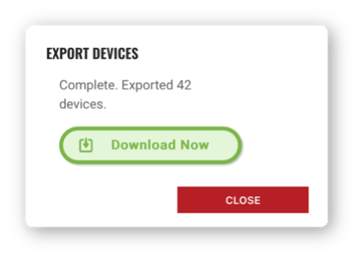
After processing, click the Download Now button in the dialog to download the CSV file of your device inventory. The file name will include a date and timestamp to make it easy identify when the file was processed. Click the Close button after you have downloaded the CSV file.
You can also export a specific set of devices based on filters (e.g., Online Now) or a search query (e.g., iPhone). First, execute the search query so only the devices of interest are shown in the list. Then click the Export button in the top right corner and select Export Results. After processing, you can download the CSV file that includes only the filtered list of devices.
Detailed Insights into Authorized Devices
One of the pillars of a modern Zero Trust Architecture is understanding the health and status of all authorized devices and using that information to control access and inform risk decisions. With detailed insights, you get detailed, real-time information about each device to make informed decisions on granting or blocking access based on policy.
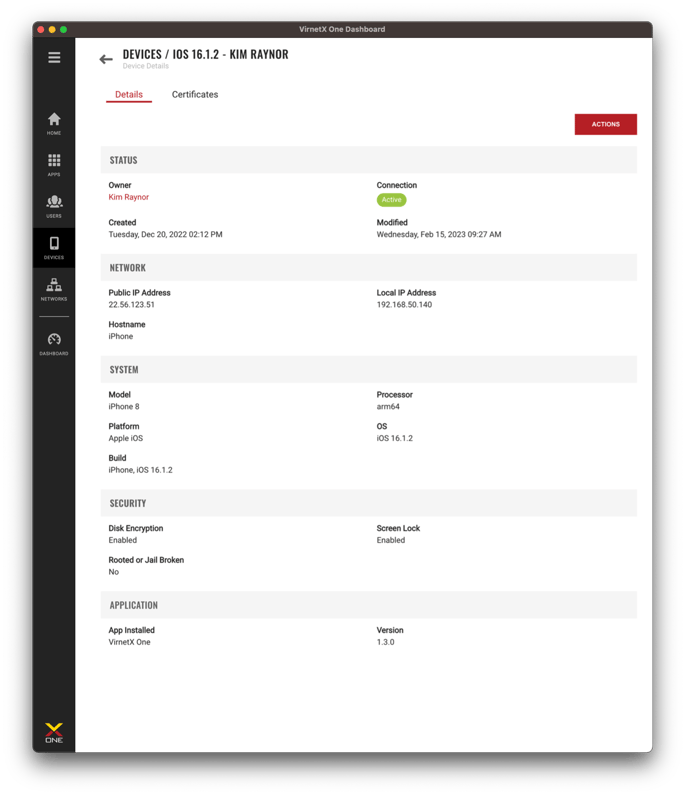
The VirnetX One client installed on each device, captures real-time, detailed information about all the authorized devices on your networks. This information includes device specific information, network information, security details, connection status and client application details. This information is updated in real-time when device system, security or network changes occur and can be used to make decisions on security posture and access. Based on these device insights, administrators can decide to temporarily block or permanently remove access for individual devices.
You can access the detailed device insights by clicking on any device of interest on the device inventory page.
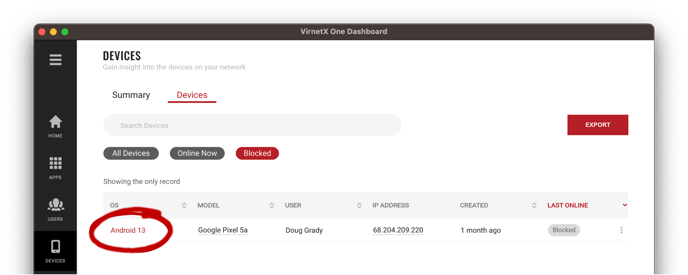
Device Attributes Collected
The following table lists all the attributes collected and the platforms where they are supported. All platforms supported includes Windows, macOS, iOS, Android and Linux.
|
Attribute |
Description |
Platforms Supported |
|
Platform |
The category of the device grouped by the operating system. |
All |
|
Owner |
The name of the user that owns the device. |
All |
|
System Name |
The “friendly name” of the device, set by the user or the DNS hostname. |
All |
|
Make |
The manufacturer of the device. |
Windows, macOS, iOS, Android |
|
Model |
The model name of the device. |
Windows, macOS, iOS, Android |
|
Architecture |
The processor architecture of the device. |
All |
|
OS Name |
The name of the operating system. |
All |
|
OS Version |
The numerical version of the operating system. |
All |
|
OS Build |
The specific build identifier of the operating system. |
Windows, macOS, iOS, Android |
|
Connection |
Connection state of the device. |
All |
|
Last Active Connection |
Date and time stamp of the last active connection to the VirnetX One platform. |
All |
|
Public IP Address |
The public IP address of the device. |
All |
|
Local IP Address |
The local network IP address of the device. |
All |
|
Blocked |
Blocked from connecting to secured resources. |
All |
|
Blocked Reason |
Reason given by an Administrator or Analyst when the device is blocked. |
All |
|
Client Version |
The version of the VirnetX One client running on the device. |
All |
|
Unapplied security patches |
The device operating system has unapplied security patches. |
macOS, Linux |
|
Jailbroken or rooted |
The device is jailbroken or rooted. |
iOS |
|
Antivirus enabled |
The device has antivirus software enabled. |
Windows |
|
Screen lock enabled |
Screen lock is enabled on the device. |
iOS |
|
Disk encryption enabled |
The disk is encrypted on the device. |
Windows, macOS, iOS |
|
Firewall enabled |
The firewall is enabled on the device. |
macOS |
|
Requires reboot |
The device requires a reboot to install software patches. |
Linux |
Block Access to Matrix Secured Applications
Using device health and status to guide access control decisions and block device access to prevent threats are important components of a Zero Trust Architecture.
Using the VirnetX One Admin Console, administrators can immediately block a device’s (e.g., mobile or laptop) access to any applications, services or infrastructure secured by Matrix. You have the flexibility to remove devices missing critical operating system updates or contain, mitigate and investigate threats and breaches.
While blocked, the device will not have access to any applications, services or infrastructure secured by Matrix. For security reasons, the user of the blocked device will also be restricted from activating any new devices while their device is blocked.
While the device is in a blocked state, you can continually assess the state and metrics on the device as a source of threat data. Once the threat or update requirement has been resolved, the device can be allowed back into the network by the administration. If not resolved, the administrator can delete the device, which permanently removes Matrix access from the device for all applications, services and infrastructure where the user had access.
How to Block a Device
Find the specific device you want to block either from the device inventory or the detailed device view.
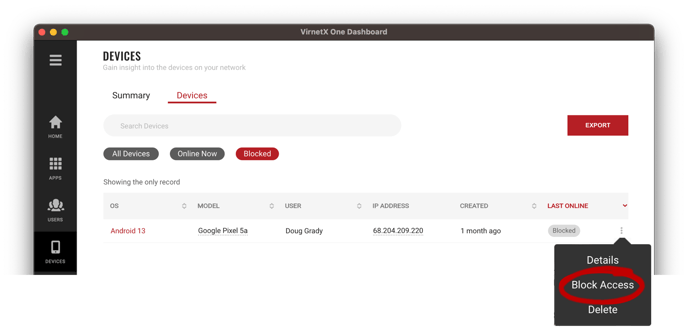
From the Device Inventory, select the three-dot menu on the right-side of the row and then click Block Access. A block device access dialog will confirm that you want to block this device and disable all connections now and in the future.
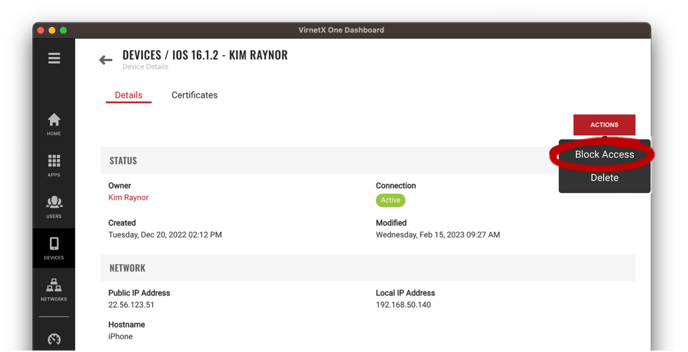
Alternatively, you can block device access from the Device Details page and click the Actions button, then Block Access from the pop-up menu.
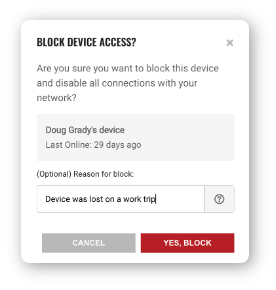
When you block access for a device, you can specify an optional reason the block was put in place. This serves as a reminder and allows other administrators to see why the block was issued before taking action.
Click the Yes, Block button to confirm. All application access will be immediately blocked and any future connections revoked. The device will no longer have access to any applications or services of the user.
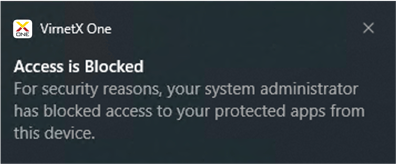
A system notification is generated on the blocked device running the VirnetX One Mobile & Desktop client to notify the user that their access has been blocked for security reasons. All access to applications, servers and infrastructure secured by Matrix will be blocked immediately.
Below is an example system notification a user with a blocked device will see on macOS.
Managing Blocked Devices
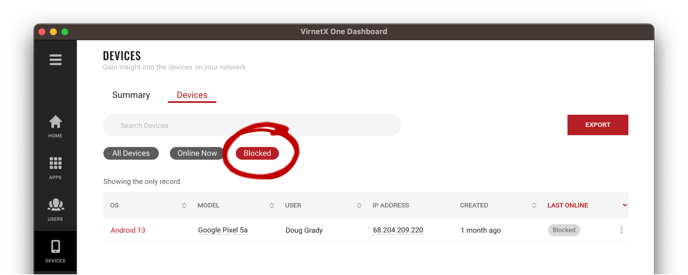
You can use the Blocked filter, found below the search box on the Devices tab, to quickly view all blocked devices. Easily view the details on a particular device, including the reason the device was blocked, by clicking on the device row or selecting the three-dot menu on the right-side of the row and then clicking Details from the pop-up.
You can continually assess the state and metrics on the blocked device as a source of threat data. Once the threat has been resolved, the device can be allowed back into the network by the IT administration, based on policy. If not resolved, the IT Administrator can delete the device, which permanently removes all access.
Allowing Access to a Blocked Device
You can allow access to a blocked device once any security or threat issues have been resolved.
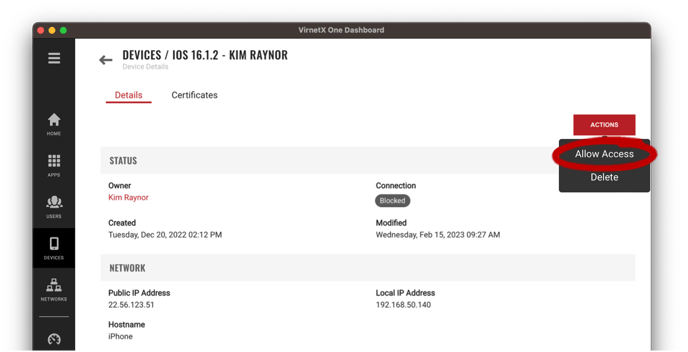
From the Device Inventory, select the three-dot menu on the right-side of the row and then click Allow Access. The device will no longer be blocked and can immediately establish new connections based on policy and permissions.
Alternatively, you can allow device access from the Device Details page and by clicking the Actions button, then Allow Access from the pop-up menu. The Connection status will change from Blocked to Offline.
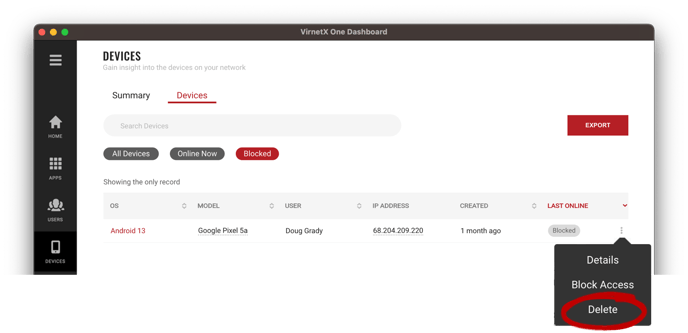
Removing or Deleting a Device
Deleting a device removes access from any application, services or infrastructure secured by Matrix. An authorized user can register the device again after deletion, based on organization policy and permissions.
Delete a device from the device insights by selecting the three-dot menu on the right-side of the row of the device you want to delete and then click Delete. Confirm you want to delete the device and it will be deleted. Access the device had to any application, services or infrastructure secured by Matrix will be removed.